Merak Email Server: Secured Destinations
Abstract
Merak Email Server offers new industry-unique feature to secure connections to remote servers using industry-standard SSL technology in combination with DNS spoofing countermeasures. Any client session (be it POP3, IMAP or SMTP) may be validated and verified against combination of user-specified conditions.
Full Text
Merak Email Server is the first in the world mailserver capable of locked-down connections to remote destinations using industry- standard SSL technology. Any client session (POP3, IMAP or SMTP) may be validated and verified against combination of user-specified conditions. This feature is located in Certificates node of Merak Windows administration console under Secure Destinations tab:
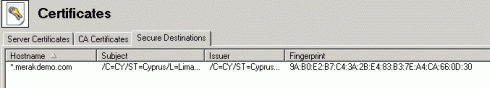
It is possible to use wildcards in hostnames (like *.merakdemo.com) taking benefit of the commercially available wildcard PKI certificates.
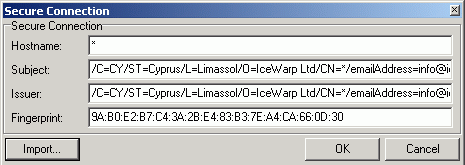
The import button located in the bottom part of the panel allows you to import the public certificate part, thus prefilling all available fields that will be checked for each client session. It is also possible to fill the fields by hand. The underlying SSL architecture is very strict:
- If SSL lockdown is requested and the SSL session cannot be established, the connection is rejected and mail returned.
- If SSL lockdown is requested but the remote server's SSL certificate cannot be validated against the conditions you defined for the host, the connection is rejected and mail returned.
The new Mail Service → Routing option allows one to lock any specified domain to a hostname or IP address, or combination of both, thus preventing DNS spoofing and poisoning.
Glossary
Hostname: Identifies the Domain Name of the host that you request strict checking for. Hostname also supports wildcards to take benefit of the commercially available wildcards certificates.
Subject: A specially formatted name that uniquely identifies the subject of a certificate. The entity that is identified by a certificate – in particular, the subject field of a certificate contains the certified entity's subject name, organization and other properties.
Issuer: The Certification Authority that issued the certificate. Please take care selecting the trusted Certification Authorities.
Fingerprint: A unique identifier associated with a certificate. This identified is not part of the certificate itself but is produced by applying a mathematical function to the contents of the public key contained within a certificate. If the contents of the certificate change, even by a single character, the function produces a different number. Certificate fingerprints can therefore be used to verify the certificate used by the remote server.
